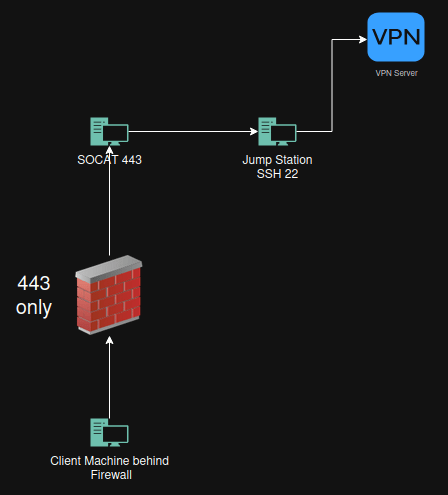
Goal Bypass firewall to get out with ssh Bypass firewall to use VPN client inside network that blocks for example Fortinet vpn client on port 443 Bypass firewall to get access to get to a machine inside my own network. Why this works Why This Works Simply running SSH on port 443 does not bypass... Continue Reading →
Heads-up: Veeam Backup & Replication Upgrade from v12 to v13 all jobs fail with error: Error: Timeout to start agent
In the affected scenario: The upgrade from v12 to v13 completes without errors All Veeam services start and run normally Proxy servers are online and show no warnings or errors Both existing and newly created jobs fail Despite everything looking healthy, every job fails with the same error: Timeout to start Agent This can be... Continue Reading →
Installing steam in Ubuntu 25.10 just to play one game Grey Hack! i386 vs 64bit, nvidia drivers dependencies, snap store issues with steam. SOLVED!
Hi! This is not a normal post, but it is related to hacking because a friend showed me a game that I really wanna try, Grey Hack. I am not a gamer (yes Dungeons & Dragons in the 80's). So this is new for me. I have a laptop with NVIDIA card so I thought... Continue Reading →
Hacking APIs: Understanding, Challenges, and Best Practices
I was doing a talk about Hacking APIs @ Plattform Summit 2025. Here is the presentation and all the commands. Applications / Toolshttps://www.apisec.ai/https://cloud.apisecapps.com/https://www.usebruno.com/ Educationhttps://www.home.apimasters.io/learnhttps://www.apisecuniversity.com/ crAPIhttps://github.com/OWASP/crAPI/bhttp://crapi.apisec.ai/loginhttp://crapi2.apisec.ai/login Information:https://danaepp.com/https://nordicapis.com/api Installation Install kali BurpSuitesudo apt-get install burpsuite Brunohttps://www.usebruno.com/downloadssudo apt-get install ./bruno_2.11.0_amd64_linux.deb FireFoxFoxyProxy Burpsuite Certifcatehttp://burpsuite Mitmproxy Certificatehttp://mitm.it Postmansudo wget https://dl.pstmn.io/download/latest/linux64 -O postman-linux-x64.tar.gz && sudo tar -xvzf postman-linux-x64.tar.gz -C /opt &&... Continue Reading →
What do I think of the Designing and Implementing API Systems course from apimasters with Mike Amundsen
In today’s interconnected digital world, APIs those quiet enablers of data exchange power everything from your favorite apps to complex enterprise systems. Yet for many professionals APIs still feel like a black box technical, mysterious and not something they need to “understand” to do their job. That’s where this API Learning Path with Mike Amundsen... Continue Reading →
What do I think of the Getting Started in API Pen-Testing from APIsec University with Teresa Pereira
If you’re curious about diving into API security and want to learn how to test APIs like a pro, you’re in the right place. The Getting Started in API Pen-Testing course by Teresa Pereira breaks down everything you need to know from the basics of common API attack methods to hands-on testing tips. You’ll get... Continue Reading →
What do I think of the Building Security into AI from APIsec University with Robert Herbig
As AI becomes a bigger part of our apps and systems, it’s also becoming a new target for cyber threats. This course, Building Security into AI is all about helping you understand where those risks come from and what you can actually do about them. Taught by Robert Herbig an experienced AI practitioner and security... Continue Reading →
What do I think of the API Security Fundamentals from APIsec University with Dan Barahona
Just finished the API Security Fundamentals course from APIsec University with Dan Barahona and it was packed with solid insights. Coming from the hacking side I usually focus on how to break things, but this course gave me a broader view of why APIs are such attractive targets and how attackers actually approach them. My... Continue Reading →
What do I think of the API Product Management Masterclass from APIsec University with Erik Wilde, Mike Amundsen, Audrey Kolski, Jeremy Glassenberg, Ilona Koren-Deutsch and Gabrielle Botbol
APIs do a lot more than just move data they’re a big part of how modern products work. This free learning path is a solid intro to how APIs are planned, designed, documented and kept secure. It is made for people who are new to API product roles or just want to better understand how... Continue Reading →
What do I think of the API Security in DevSecOps from APIsec University with Scott Bly
APIs are everywhere and so are the risks. If you're working in DevOps or dev teams and want to build more secure apps the API Security in the World of DevSecOps course from APIsec University is a solid place to start. It’s free, practical and perfect for anyone looking to bring security into their development... Continue Reading →
What do I think of the Hacking Enterprises 2025 Edition course from In.Security with Will Hunt?
Offensive security courses are everywhere these days, but very few truly deliver a deep, hands-on experience that feels like the real deal. I recently completed the Hacking Enterprises 2025 Edition course from In.Security, led by Will Hunt, and after taking it twice now, I’m excited to share what makes this course stand out. Personal Experience... Continue Reading →
What do I think of the Detection Engineering for Beginners course from TCM Security with Anthony Isherwood?
I recently finished the Detection Engineering for Beginners course by TCM Security, taught by Anthony Isherwood. As always, I’ll keep this post short and focused just like the course claimed to be "for beginners"… more on that below. My Thoughts Let’s start with this: not every course is for everybody and that’s perfectly fine. The... Continue Reading →
What do I think of Security Operations (SOC) 101 from TCM Security with Andrew Prince
It’s not often that a course leaves me this impressed. Security Operations (SOC) 101 by Andrew Prince over at TCM Security is one of the most comprehensive courses I’ve taken in a long time and that’s saying a lot. This course doesn’t just cover SOC. It dives deep into everything surrounding it endpoint security, phishing... Continue Reading →
What do I think of Practical Windows Forensics course from TCM Security with Markus Schober
It’s been a while since my last post! Life and work got in the way, but I’m back and hoping to put out many more posts this year! Now, let’s dive into this amazing course—ractical Windows Forensics from TCM Security, taught by Markus Schober. If you're interested in Windows forensics, digital investigations, and incident response,... Continue Reading →
Securing LLM & NLP APIs: Lessons from APIuniversity
Securing LLM & NLP APIs: Lessons from APIuniversity As the use of large language models (LLMs) and generative AI continues to grow, so does the importance of understanding how to secure these technologies effectively. Recently, I completed the Securing LLM & NLP APIs course from APIuniversity, an essential training that arms developers, data scientists, and... Continue Reading →
What do I think of passing the ASCP exam from Apisec University
Passing the ASCP (API Security Certified Professional) exam is a notable achievement for anyone in the field of API security. APIsec University provides a structured and comprehensive approach to prepare for this challenging exam, and I can vouch for its effectiveness. Here are my thoughts on the experience and some advice for future candidates.Sign up... Continue Reading →
What do I think of the Practical Phishing Campaigns course from TCM Security with Aaron Wilson
Who should take this course? The Practical Phishing Campaigns course from TCM Security is tailored for a wide range of individuals within the cybersecurity domain. If you're a penetration tester, security analyst, or system administrator looking to enhance your phishing campaign skills, this course is ideal for you. It's also beneficial for those who have... Continue Reading →
What do I think of Practical Bug Bounty course from TCM Security with Heath Adam, Alex Olsen, and Jonah Burgess from Intigriti
The Practical Bug Bounty course by TCM Security, led by Heath Adams, Alex Olsen, and Jonah Burgess from Intigriti, is a thorough exploration of hacking and web application security. Alex's extensive knowledge and Heath's significant community contributions are evident throughout the course. Despite its focus on bug bounty hunting, the course offers a wide range... Continue Reading →
What do I think of Practical Web Hacking course from TCM Security with Alex Olsen
Web security is an ever-evolving field, requiring continuous learning and adaptation. TCM's course "Practical Web Hacking," led by the exceptional instructor Alex Olsen, is designed to equip cybersecurity enthusiasts and professionals with hands-on knowledge and skills to tackle real-world web security challenges. This blog post delves into what this course offers, who should consider enrolling,... Continue Reading →
What do I think of API Authentication course from APIsec University with Jacob Ideskog from Curity
In the ever-evolving landscape of digital interactions, ensuring secure communication between clients and servers is paramount. API authentication and authorization are fundamental concepts that protect sensitive data and ensure that only authorized users can access specific resources. In this blog post, we will explore key aspects of API authentication and authorization, drawing insights from the... Continue Reading →
What do I think of Practical API Hacking Testing course from TCM Security with Alex Olsen
Hi! As someone who has recently completed the Practical API Hacking Testing course from TCM Security, taught by Alex Olsen, I wanted to share my thoughts and experiences. This course is designed to provide comprehensive knowledge and practical skills for testing and securing APIs, an increasingly critical area in cybersecurity. As a final word I... Continue Reading →
Just completed the Securing API Server Course from @apisecu with Anthony Aragues! 🛡️ Fantastic insights into API security. Highly recommend it for anyone in the field. #APIsecurity #CyberSecurity @Burp_Suite #OWASP
Enhancing API Server Security: Best Practices from APISec University Introduction: API servers play a pivotal role in modern application architecture, enabling seamless communication between different software components. However, with this convenience comes the responsibility of ensuring robust security measures to safeguard sensitive data and prevent unauthorized access. In this blog post, we'll delve into various... Continue Reading →
Secbutler is cool tool to have in your toolbox when doing fun stuff like Pentesting, CTF or just having fun. Cheatsheets, listeners, revshells and more.
Hi! Link to tool: https://github.com/groundsec/secbutler Exploring Secbutler: A CLI-Based Security Tool I recently stumbled upon a gem in the realm of cybersecurity tools – Secbutler from Groundsec. In a world saturated with graphical interfaces and web-based platforms, Secbutler caught my attention for its command-line interface (CLI) approach. Now, you might be wondering, why make an... Continue Reading →
Create a hacker machine that supports Andriod, Web and API. What to install an how to install.
Start I have a laptop running Kali and Virtual Box with a kali vm on it. I wanted to have a setup that is easy to copy, backup and restore and the main tools installed. Here is the steps that I took to get this setup up and running. Where did I get this information... Continue Reading →
Creating a seamless multi-OS environment. Running Linux and Windows and share data easy with insync between OS and running shared config for applications like Remote Manager.
Hi! I got it working last night and wanted to share the news with you. Goal Ensuring uniform configurations across diverse operating systems poses a notable challenge. In the initial scenario, the objective is to deploy a remote application consistently across all machines, maintaining identical configurations. Furthermore, this requirement extends to encompass a broader spectrum.... Continue Reading →
Why you want to be apart of security community with Antisyphontraining, Black Hills Information Security (BHIS), Activecountermeasures and wildwesthackinfest.
Unwrapping the Gift of Cybersecurity: A Pleasant Surprise in 2024! In a delightful twist of fate, I recently received an email that added an unexpected sparkle to my year. Whether it's a belated Christmas present from 2023, an early one for 2024, or just a stroke of good luck coinciding with my current phase in... Continue Reading →
SMARTSCREEN ERROR when using Edge for my site. For some reason I am on the bad list! I am trying to fix that. UPDATE After a few days Microsoft fixed this after I filled in request a couple of time!
What do I think of Programming with AI – Mini Course from TCM Security with Heath Adams
Hi! Embarking on the journey of programming with artificial intelligence doesn't require an extensive background in coding wizardry. In fact, TCM Security's "Programming with AI - Mini Course" with Heath Adams is meticulously designed to be accessible to individuals with a basic understanding of programming fundamentals. Whether you're a cybersecurity enthusiast, a software developer, or... Continue Reading →
What do I think of Mobile Application Penetration Testing course from TCM Security with Aaron Wilson
Hi! In a world dominated by mobile apps, the importance of securing them cannot be overstated. My journey into mobile application pentesting began with a realization of the vulnerabilities these apps may harbor. Seeking a comprehensive course, I stumbled upon the TCM Security Mobile Application Penetration Testing course , and little did I know it... Continue Reading →
What do I think of Linux101 course from TCM Security and the really nice voice from @brenteskridge
Hi! As we ushered in the new year, my company made a savvy move by subscribing to TCM Security for a year. I wasted no time diving into the first course on my list – Linux 101. Trust me when I say, it's not just for beginners seasoned Linux users will find hidden gems too.... Continue Reading →
Knowledge schedule for 2024.
Embarking on the journey of 2024, I've already shared glimpses of my set goals, and now, it's the opportune moment to intricately document this path. This endeavor serves not only as a testament to my personal aspirations but also as an inspiration for you—proving that the pursuit of your dreams is not only worthwhile but... Continue Reading →
What are the plans for 2024 for my infosec knowledge update?
Remeber that repetion is the mother of knowledge. --Roger-- I have not been very active on the blogg in 2023, sorry for that. I hope I can change that for 2024 What is the goals for 2024 There has been some changes for 2024 regarding education budget, so I will need to do some changes for... Continue Reading →
Install & Configure for Success: Free Load Balancing DNS & UDP with LoadMaster 🚀
Hi! When I was looking into HA with haproxy I stumble up on LoadMaster from Progress, yes they bought Kemp company in 2021. I wanted to create a almost free soloution for ntp, dns services on the network and HAproxy can not to udp (what I know). Today we are gonna test the free version... Continue Reading →
Elevate your web services with high availability clusters and HAProxy load balancing! 🚀 Discover the synergy that ensures seamless operations.
Hi! I am on a strike! This time we are divning into haproxy and how to make a HighAvilable cluster with HA proxy We start of with the big steps. Install OS (ubuntu in mine case) Configure HA cluster with keepalived Install haproxy Test Goal I wanted a proxy soloution that hade failover, so I... Continue Reading →
Set up a POC for Proxmox and Ceph storage HCI cluster with backup soloution with VirtualBox.
Hi! First post in a long time, it is time to get into Proxmox hypervisor soloution. I did not have any hardware for testing so I did the setup in VirtualBox on my laptop. Setup VirtualBox Install Proxmox Install ceph storage cluster Install Proxmox Backup Test it Goal Here is picture for the goal of... Continue Reading →
Learn how to hack and how to secure your api, and do it for free. API Penetration Testing, OWASP API Security Top 10 and Beyond, API Security Fundamentals, Cross Origin Resource Sharing (CORS) and Error Disclosure.
Hi! It has been some time now between the posts, but life is getting in the way. The hard thing about security is that you will never learn enough you will need to educate your self all the time, new stuff comes out, new technology. It is nice that knowledge is easy to carry. 🙂... Continue Reading →
vSphere – Lifecycle Manager stops at remediation at 30% and install stops at 0% then errors out after 41 minutes. @vExpert #vExpert #esxi #Virtualization @VMware
Hi all! Time for some VMware stuff now! I was planing to do patchning this weekend, and I always try on test servers first. But this time it failed. I want to get out the word how I fixed that issue. If you will do this you will loose the baseline that you created. Versions... Continue Reading →
Passed this fantastic course API Penetration Testing Course from @apisecu with @hAPI_hacker. This is my review after finishing the course. #hacking @Burp_Suite #zapproxy #hacking #api @owasp
Hi! Today I want to say a few words about a course I finished yesterday night! This review could have been a one liner: Take this course, if you don’t you are missing something really cool! Big shout out for making this possible. Really great work! https://www.apisecuniversity.com/ Corey J. Ball https://www.linkedin.com/in/coreyjball/ https://twitter.com/hAPI_hacker Dan Barahona https://www.linkedin.com/in/rdbarahona/ https://twitter.com/danbarahona But I want... Continue Reading →
My plan almost worked. Got #OSCP certified from @offsectraining. Something need to be said. Thanx to @WWHackinFest @BHinfoSecurity @strandjs @BanjoCrashland @debthedeb and many more.
Hi! I made it! Intro Lets face it the IT industry has changed a lot the past almost 30 years that I have been in this amazing bubble. If you are in the same shoes as med and want to learn something new like I did 2018 then this is for you. (at least I... Continue Reading →
How to find hardware issues with SQL errors in an vmware environment. A read of the file at offset succeeded after failing 1 time(s) with error: incorrect pageid #vExpert @VMwarevSphere #esxi #database #sql #sqlserver #microsoft
I ran into som very strange problem on an SQL server this fall that I need to tell you about. The Error A read of the file 'D:\SQL PATH\Data.mdf' at offset 0x0000001ad60000 succeeded after failing 1 time(s) with error: incorrect pageid (expected 1:214336; actual 14854:3166640). Even if we see these error SQL was able to... Continue Reading →
Impossible to remove Advanced Settings on Vcenter object or not? #vExpert @VMwarevSphere #esxi #virtualcenter
I my post before I explained how to fix a corrupt VCLs. When I did this in the lab I misspelled the setting. When I pasted the cluster number in the advanced setting I copy and paste the hole url for some stupid reason. When you do that it is not possible to add the... Continue Reading →
What can you do when your cluster vcls are corrupt or do not boot? #vExpert @VMwarevSphere #esxi
Hi! I upgraded some vmware cluster and stumble up on VCLS machine on high cpu usages. That is strange, because these are small machines and should not take any cpu normally. And you can not do anything about it. You can shut the machine down, but it will start up again. In my case the... Continue Reading →
Failed the #oscp, what happens now? Pros and Cons regarding @offsectraining and there Learn One Annual Subscription. #i_still_wanna_be_an_oscp_certified_nerd
Hi! First of I don't heckle any knowledge or any company, this is my view of my world! And because I failed this one I can not do a comparison between the certification that I have and this one. I hope it is coming in 2023 🙂 I will have a meeting with @offsectraining, and... Continue Reading →
After upgrade from #esxi 6.7 to 7.0.3 unable to live migrate vm:s with nvidia v:gpu enabled. @NVIDIA @VMware @vExpert @vmwarehorizon
The goal of this action was to upgrade a cluster with nvidia graphics card from 6.7 to 7.0.3. Before the upgrade everything worked fine. You where able to live vmotion vm:s with vgpu to another host. Problem: Everything worked from vm side, but was not able to vmotion live vm:s between hosts. Steps: Upgrade esxi... Continue Reading →
PNPT Exam review and how did I approach the exam. Delivered by @TCMSecurity @thecybermentor #Cybersecurity #hacking
I must start saying that this exam was great. I started doing practical exam during my Novell eDirectory 991 course back in the days. And I loved them. This is another exam that I must say goes to my heart. I love the practical stuff. One other thing to say about this exam is that... Continue Reading →
Review on Practical Web Application Security and Testing from @TCMSecurity and @mttaggart learn @owasp #hacking #education #almostfree
Hi! I do this one more time then I need to go back to the original schedule read here : https://blog.invid.eu/2022/01/06/my-ocsp-and-pnpt-journey-from-the-beginning-during-and-i-hope-the-end-tcmsecurity-thecybermentor-offsectraining-pnpt-oscp-joplinapp-reconmap-bhinfosecurity-strandjs-hacking-pentesting/ I did find this course very helpful so I need to say a few words. This course was amazing. One thing stands out from any other web course. After you finish the course you... Continue Reading →
Review on Practical Malware Analysis & Triage from @TCMSecurity and @HuskyHacksMK #malware #hacking #education #almostfree
Hi It is not often I do a post a review of web courses except in my journey post https://blog.invid.eu/2022/01/06/my-ocsp-and-pnpt-journey-from-the-beginning-during-and-i-hope-the-end-tcmsecurity-thecybermentor-offsectraining-pnpt-oscp-joplinapp-reconmap-bhinfosecurity-strandjs-hacking-pentesting/ But I did find this course so dam good that I need to shout it out. This course was amazing. I learned alot, new stuff for me. Matt Kiely @HuskyHacksMK who was the teacher is amazing,... Continue Reading →
How did I pass OSWP exam? Tips and Tricks. @offsectraining #PEN-210 #hacking #pentesting #wireless #INVID #dyslexia
Hi! Today I received my first certification from Offensive-Security (not counting PEN-100). If someone else is in progress of taking this course or thinking about it here are my tips and tricks. Here are some links from offensive security that you shall read if you will attend an exam from Offensive-Security. Verification https://www.credential.net/bac14e8c-24e1-43c5-a2c7-8d0751543caa Links https://help.offensive-security.com/hc/en-us/articles/360046904731 https://proctoring.offensive-security.com/student/login https://help.offensive-security.com/hc/en-us/sections/360008126631 https://help.offensive-security.com/hc/en-us/articles/360050299352 https://www.offensive-security.com/legal-docs https://help.offensive-security.com/hc/en-us/articles/360046293832 ... Continue Reading →
How to crack wireless networks. To get ready for PEN-210 OSWP certification. (For educational purpose only) @offsectraining #INVID Gruppen #OSWP #PEN-210
Time to do some wireless hacking. If you read my other posts you know that I am on a mission get OSCP. But sometimes you need to do something else. This is my attempt to do something else 🙂 Todo what I do in this post you need some hardware. At least a network card... Continue Reading →
What you need to know to prepare for OSCP exam? Or what I need to know. Labs, Reporting and Exam requirements. #OSCP #pentesting @offsectraining
Hi! I am preparing for the OSCP exam, and there is alot of information out there. I needed to know what I am suppose to know before I take the exam. If you are about to do this exam please read the links, I know there is a lot text, but it is important. My... Continue Reading →
Free AWS education – AWS Technical Essentials and AWS Cloud Practitioner Essenstials. @awscloud #AWS #cloud #CloudComputing
Hi! Between Offensive Security and TCM Academy courses I was able to do the online course from AWS. The nice thing about the online ones is that you can ask questions during the course. But these course are also availble for free on AWS traning site. I can highly recommend these if you are new... Continue Reading →
Governance, Risk and Compliance (GRC) Analys Master Class with @Gerald_Auger #SimplyCyber @NIST #cybersecurity #education
I did take a small break today from Offensive Security today and found a realy nice course, not so practical but still very important. If some of below words is picking your brain this course is for youA Cybersecurity Primer, Compliance and Audit Work, Security Awareness Work, Cybersecurity Risk Work, Information Security Governance Work, Getting... Continue Reading →
Eat, Drink, Sleep and Shit security. How in a “easy” way keep you updated on what is happening out there. @BHinfoSecurity @ActiveCmeasures @WWHackinFest @intigriti #security #knowledge
How do you keep you updated on what is happening out there, I have some tools and workflow that will keep you busy. One thing you need to think about, not everything on the internet is the truth.The hard thing here is that there is endless information out there, but yo do not need to... Continue Reading →
Upgrade EOL Ubuntu server from 20.10 to 21.10. An upgrade from ‘groovy’ to ‘impish’ is not supported with this tool. @ubuntu @ubuntugeek #ubuntu #linux #EOL #upgrade
Hi all! Time to do a quick post that ran into this evening. As always I update my lab to be on the latest version all the time. But this one time I missed a machine. 🙂 We begin with EOL version of Ubuntu 20.10 The below picture says that we have a new version... Continue Reading →
How to document ActiveDirectory free and with #powerhsell export to excel and word #ActiveDirectory #documentation @evotecpl
Hi! As I am not writing alot of other stuff other than my goal to PNTP and OSCP right now ( https://blog.invid.eu/2022/01/06/my-ocsp-and-pnpt-journey-from-the-beginning-during-and-i-hope-the-end-tcmsecurity-thecybermentor-offsectraining-pnpt-oscp-joplinapp-reconmap-bhinfosecurity-strandjs-hacking-pentesting/ ). But in this case I have to. I was looking for a simple way to document a new customers Active Directory. How shall I do that in a easy way? I had... Continue Reading →
My OSCP and PNPT journey from the beginning, during and I hope “the end”. @TCMSecurity @thecybermentor @offsectraining #PEN-100 #PEN-103 #PEN-200 #PEN-203 #WEB-100 #SOC-100 #PNPT #OSCP @joplinapp @reconmap @BHinfoSecurity @ActiveCmeasures @WWHackinFest @strandjs #hacking #pentesting
Intro Hi all! My plan is that under 2022 to take OSCP and PNPT exam. To get the full picture we start from the beginning. Why do I post this? Share knowledge is the simple answer, and I am getting old so I need to document everything I do. I think this is a good... Continue Reading →
Podcasts you need to take a look at. @DarknetDiaries @DanielMiessler @IntelTechniques @InfosecEdu @7MinSec @coalfirelabs @NetSPI @breachsense @TrustedSec @riskybusiness @thehackscast@NakedSecurity @thehackerish @CyberSpeaksLIVE @BHinfoSecurity @PentesterLand @itsakerhetspodd @geoffwhite247 @CSI_Podcast
Here are podcasts that I like to listen to when I can. It is not best to worst list it is only a list!Some of them has not been updated for some time, but still check them out. https://darknetdiaries.com/https://twitter.com/DarknetDiaries https://danielmiessler.com/podcast/https://twitter.com/DanielMiessler https://inteltechniques.com/podcast.htmlhttps://twitter.com/IntelTechniques https://breachsense.io/https://twitter.com/breachsense https://thehacks.libsyn.com/websitehttps://twitter.com/thehackscast https://nakedsecurity.sophos.com/https://twitter.com/NakedSecurity https://thehackerish.com/https://twitter.com/thehackerish https://7ms.us/https://twitter.com/7MinSec https://www.netspi.com/agentofinfluence/https://twitter.com/NetSPI https://www.blackhillsinfosec.com/https://twitter.com/BHinfoSecurity https://risky.biz/https://twitter.com/riskybusiness https://www.trustedsec.com/podcasts/https://twitter.com/TrustedSec https://www.infosecinstitute.com/podcast/https://twitter.com/infosecedu https://coalcast.libsyn.com/website/category/Coalfirehttps://twitter.com/coalfirelabs https://pentester.land/https://twitter.com/pentesterland https://www.mcafee.com/en-us/consumer-support/podcast.htmlhttps://twitter.com/McAfee https://coinsecpodcast.com/https://twitter.com/CoinSecPodcast... Continue Reading →
Courses and Certifications that I have taking over the years. Knowledge is the key.
If you are interested in any just send me an email if you want information about them. This is mostly a reference page to other bloggposts. BHIS Webcast: Things NOT to Do in Pentest Reports: Tips, Tricks 2023-02-03 Future Red Team Rants: A breakdown in three parts 2023-01-26 All About Ansible - A Suite of... Continue Reading →
Open-Source Vulnerability Assessment and Pentesting Management Platform @reconmap #pentesting #opensource #hacking #opensource #cybersecurity
Hi again! Time to look at reconmap. We in this line of work love abbreviation, so I call this OVAPMP (Vulnerability Assessment and Pentesting Management Platform). I was looking for a tool/system documenting my work regarding vulnerability scans, pentest and bug bounty work. I have tried different kind of solutions, I think I have found the... Continue Reading →
DarkWeb tools, how to install and run @torproject @TebbaaX @splitgraph @sn1persecurity @DarkSearchApp #pentest #readteam #hacking
Hi! It is time to go dark. In this post we are gonna take a look at different tools that is out there for the not so light web. This post is not for you to learn how to go dark, it is for people to learn how things works. Do not go and do... Continue Reading →
Install, build and run Sn1per. Testing the free version. @Sn1perSecurity #attacksurface #infosec #assetmanagement #attacksurfacediscovery #bugbounty #platform #netsec #offsec #redteam #pentest #attacksurfacemanagement
Hi all out there. It is time to take a look at sn1per. A tool that automate opensource stuff for us. As always we start with the steps Install some os in my kase running kaliGet the docker fileBuildRun sn1per installation wget https://raw.githubusercontent.com/1N3/Sn1per/master/Dockerfile docker build -t sn1per . Below is gonna take some time to... Continue Reading →
How to approach security by learning or really any learning (my way) @albinowax @jaybeale @ralphte1 @goteleport @CyberDefenders @BanjoCrashland @BHinfoSecurity @dayzerosec @NakedSecurity @cert_se #pentest #PENTESTING #redteam #infosec
First thanx to all mention in this post! The hard thing about security is the wide range of stuff you have to learn if you wanna be the best. That is the goal you should have, I want to be the best. But the downside of this is that how do I learn everything, I... Continue Reading →
My thoughts about C2 and the tests @C2_MATRIX @metasploit @c2_matrix #Covenant @BYT3BL33D3R @BHinfoSecurity #PENTEST #PENTESTING #REDTEAM #INFOSEC #autossh #ssh
Hi, this will be a short one. But I must put down in words what my thoughts are about the C2 tests that I have been doing for some time now. Not so hard to set up and get it running. If you want to play around there are some really good blog post out... Continue Reading →
Fith step in setting up C2 environment. Using socat as front to SILENTTRINITY. Command and Control my way. @c2_matrix @byt3bl33d3r @porchetta_ind #pentest #pentesting #redteam #infosec
Now we are gonna look at SILENTTRINITY from @byt3bl33d3r I think this will be the last test of Command and Controll application. I have other stuff to do. But I hope you all had a good read and set some things in motions for you. Here is the link that you can read and download... Continue Reading →
Fourth step in setting up C2 environment. Using socat as front to Covenant. Command and Control my way. @c2_matrix #Covenant #pentest #pentesting #redteam #infosec
It is time for part 4 in this series to set up a Command and Control, and this time I am trying out C2 server Covenant. You can go and read about Covenant here https://github.com/cobbr/Covenant. A picture says more than 1000 words so lets start with that! Covenant Short list install kaliapt-get updateapt full-upgradesystemctl enable... Continue Reading →
Third step in setting up C2 environment. Using socat as front to merlin. Command and Control my way. @c2_matrix @merlin_c2 #pentest #pentesting #redteam #infosec
It is time for part 3 in this series to set up a Command and Control, and this time I am trying out C2 server Merlin. You can go and read about Merlin here https://github.com/Ne0nd0g/merlin. A picture says more than 1000 words so lets start with that! Merlin The short step by step list install... Continue Reading →
Second step in setting up C2 environment. Using socat as front to autossh. Command and Control my way. @c2_matrix #autossh #ssh #pentest #pentesting #redteam #infosec
It is time for part 2 in this series to set up a Command and Control, and this time I am using ssh for creating reversed ssh tunnel to my C2-1 server. So I can run ssh from a client machine and take over this machine from my C2-1 server. A picture says more than... Continue Reading →
First steps in setting up C2 environment. Using socat as front to metsaploit. Command and Control my way. @c2_matrix @metasploit #pentest #pentesting #redteam #infosec
Hi, I know that is been a while since the last post, but life got in the way. But it is time now. My goal in these coming post is to setup different Command and Control systems and try them out. Information about different C2 can be found on this fantastic site https://www.thec2matrix.com/ So as... Continue Reading →
DELL server SD-card problem after firmware upgrade to SD Module 1.15. 2 fixes. @Dell @VMware #vExpert #esxi
After firmware upgrade of DELL server we got issue regarding SD Card mirror. Here is how we sloved this. DELL Support is informed and they are working on it. Fix would be in the next release I was told. But first Do not use SD card to boot serverEsxi will drop the support laterThere are... Continue Reading →
Add portgroups on a vswitch is pain in the *ss, but you can use this simple script to get it done. @vExpert #esxi #vswitch @VMware #vCommunity
Hi! Not everyone are using distributed switches in there vmware enviroment or the licence for host profiles. Some uses ordinary vswitches, like me. And every time I do a reinstall or add new hosts I have alot of vlans to add. You can do it from GUI, but it takes time. You can use api:s,... Continue Reading →
How to revert from NVMe controller to paravirtulized scsi controller. Blue screen inaccessible boot device when I do that. How to fix it with 2 commands #windows10 @PURESTORAGE @VMWARE #VEXPERT #ESXI #PERFORMANCE
Hi all! The latest posts has been about how to get the most of our hardware in a virtual machines. But sometimes you need to revert stuff you do. Or as me, try everything that can go wrong. When I revert from paravirtulized driver on my Windows 10 vm to NVMe controller everything went fine.... Continue Reading →
New version of hashcat is out. Time to test version 6.2.0 @HASHCAT #LINUX4HACKERS #HASHCAT #LINUX #INFOSEC #HACKING #PENTEST #PENTESTING #REDTEAM #NVIDA #BRUTEFORCE #NVIDA #TESLAM60
Hi all! There is a new version of Hashcat out for you to try! Here you can download it https://hashcat.net/hashcat/ 312 different algorithms to use. The different attack modes are: Straight, Combination, Brute-force, Hybrid dict + mask, Hybrid mask + dict and Association Fixes There is 26 bugfixes in this release. New attack mode: Association... Continue Reading →
Choose SCSI Controller to get the best performance on a VM. What SCSI controller on VM shall I use. Queue Depth settings on ESXi. Queue Depth in Windows VM. Pure Storage performance. @PureStorage @VMware #vExpert #esxi #performance
Last post I was looking at vCPU configuration on a vm to get best performance on a vm. Now it is time to take a look at performance on the disk side. To test performance I used CrystalDiskMark. Finally I was able to add a file in WordPress, the link to the file is at... Continue Reading →
Test vCPU configuration to get best performance out of a VM. What configuration shall I use. #vCPU @vExpert @VMware #virtualmachine @FrankDenneman #numa @mwVme
We start with what our goals are We have a vm that want to take as much cpu power as possible from the host. But how shall we configure the VM to make the most of it. You have read about numa nodes and what that means? right? If not look, at the bottom of... Continue Reading →
In place upgrade to Windows 2019 from Windows 2016. Error 0xC1900101 – 0x30018 The installation failed in FIRST_BOOT phase with an error during SYSPREP operation. #windows2019 @MicrosoftHelps @Microsoft
Hi all! This must be one of the first time that this happens, something about Windows in this blogg. But i felt like this must be shared. I was doing in place upgrade from Windows 2016 to 2019. And some some servers went well and some got this message. The upgrade went to about 52%... Continue Reading →
Attending Active Defense & Cyber Deception with @strandjs and want to run the WINADHD vm in ESXi, please read this. @WWHackinFest @BHinfoSecurity @ACTIVECMEASURES #ACTIVECOUNTERMEASURES #THREATHUNTING #BEACONS #WINADHD
If you attending John strand in this epic course and want to run the lab vm in Vmware ESXi please read this. If not, go and do something with your girlfriend,boyfriend or children or take a beer and relax! Hi, I am looking at a new way to work so I was not able to... Continue Reading →
Attending Cyber Threat Hunting Level 1 w/ Chris Brenton | 4-hours and want to run the VM in QEMU/KVM this is how I got it to work. @ActiveCmeasures #activecountermeasures #AIHunter #ThreatHunting #Beacons #Activecountermeasures @Zeekurity
Hi all! If you are like me attending the Threat Hunting Training Course named Cyber Threat Hunting Level 1 w/ Chris Brenton | 4-Hours on Thursday and want to run the virtual machine in qemu/kvm native do it like this. Download and read the below link! https://www.activecountermeasures.com/cyber-threat-hunting-training-course/ As always start with the short version! Convert... Continue Reading →
Using fail2ban and the see what countries are trying a little to much to connect to my server. #Fail2ban #infosec #CyberSec #linux #awk #sed @ubuntu #linux4hackers
Hi! Goal for today is to get a list of what countries is trying to much to connect to my server using fail2ban. I know this is not a good thing to have port 22 open on internet, but sometimes you need that to prove a point. Install fail2banInstall geoip-binOpen port 22 on your server... Continue Reading →
How to do remote work smooth with any device and still use camera, microphone in any application. Using my work PC as remote nod and Ubuntu as a client home. @vmware @vmwarehorizon @vExpert @ubuntu @vExpert #remote #WorkFromHome #linux
Goal for today is to connect to work machine, in this case a Windows 10 and have all the functions that I have when I am physical at work. So I had some requirements on my list. Client at home can be anything (Linux in my case)Must support camera and microphoneFastNo lagSimple to useSecure First... Continue Reading →
CEH Master, LPT, eJPT and eCPPTv2. My thoughts about the exams ,courses and how I got there. @ECCOUNCIL @eLearnSecurity @ReadynezSocial @hackthebox_eu @RealTryHackMe @BHinfoSecurity @RedSiege @WWHackinFest @ActiveCmeasures
I am gonna try to explain how my dedicated my life to work and what it takes for me to get this far. This is gonna be about the penetrations exams that I took, but I would not have passed these if I did not took the Novell Netware Networking course back in the days.... Continue Reading →
Passing the eCPPTv2 certification from eLearnSecurity. 10 answers for you to pass the exam. Thanx to @eLearnSecurity @RealTryHackMe #eCPPTv2 @thecybermentor #infosec #hacking #pentest #pentesting #redteam #hackthebox #linux4hackers #blackbox
Got the eCPPTv2 Certification today. Nice way to start the year with. 7 days of penetration testing and 7 days of report writing. Total of 14 days. This is the schedule that you get. The penetration test is in form of black box. You can use what tool you want. Why invent the wheel again?... Continue Reading →
Adding automating pentest tools for WebApi to my hacking rig. Astra and Fuzzapi. @bsdbandit @RedSiege @TimMedin @Fuzzapi0x00 #OpenSource #Security #WebServices #API #webapi
This blog will be relatively short, but I thought the webinar I listened to was so interesting that I have to write about it. Webinar from Red Siege yesterday evening (21.00 Swedish time) regarding hacking webapi. Link: https://www.redsiege.com/api/. This was presented by @bsdbandit. I was blown away, this is really cool stuff. I was the... Continue Reading →
Explain in my own way how to do basic Buffer Overflow. With help from @RealTryHackMe #BufferOverlow #Hacking #INFOSEC #LINUX4HACKERS #pentest #pentesting #redteam
First this is not advanced BufferOverflow, more for me to write down and document what I did at tryhackme to get BufferOverflow Prep working. We start of what you need. Windows 7 box with ImmunityDebugger and mona installed. Access to the application ocsp.exe. You can do this online with tryhackme or download the application your... Continue Reading →
Why would you use masks with hashcat when you crack hashes in brute force mode. @hashcat #LINUX4HACKERS #HASHCAT #LINUX #INFOSEC #HACKING #PENTEST #PENTESTING #REDTEAM #NVIDA #TESLAM60 #NTLM #BRUTEFORCE
In this post I will try to explain why it is important to use masks when you crack password from hashes with hashcat. The machine that I run hashcat on has 2 Tesla M60 card and running Linux. Why do I not use longer password in this test, I do not want to wait 7... Continue Reading →
How to export/crack SAM database with internal Windows tools if you do not have access to mimikatz / hashdump / metasploit. As a bonus we also look at cached domain hashes. #LINUX4HACKERS #HASHCAT #LINUX #INFOSEC #HACKING #PENTEST #PENTESTING #REDTEAM #NVIDA #TESLAM60
Hi! I wanted to dump hashes on a Windows 10 box without any external tools. This is how I did it. We start at first with the short version Export SAM with reg.exeConvert SAM with impacket-secretsdump to get to the hashesUse hashcat to crack the hashes We start first with exporting the sam database with... Continue Reading →
Migrate from VirtualBox to QEMU/KVM on Ubuntu 20.10 as host. And get the VMs up and running. #qemu #kvm #libvirt #virtualbox #linux #virtualbox @ubuntu
Hi! I am have been running VirtualBox for my VMs on a Linux host for some time now. But when kernel 5.10 was installed there was some issue with compiling the drivers for VirtualBox. I think there is a workaround out there, but I needed to fix this asap. So I decided to migrate to... Continue Reading →
Using MindMap application when doing pentest or ctf! Up for you to decide. #MindMaps #freesoftware #kali #linux4hackers #linux #infosec #hacking #pentest #pentesting #redteam @kalilinux #ctf #bugbountytips @insilmaril
I was thinking about a nice and easy way to save a penetration test and come up with this.Use a MindMap application.There is a alot of MindMap application out there. I am running Linux on my machine so I ended up with VYM. (http://www.insilmaril.de/vym/)The nice thing about VYM is that it is free and comes... Continue Reading →
How to get autocompletion working great instead of good in powershell for linux. #powershell #pwsh #pwsh-preview #linux @ubuntu @powershell #autocompletion
My colleague @Schillman told me that you can get better autocompletion in powershell for linux. I thought that was interesting thing to try. Soon Sebastian will see the light in the tunnel and convert to a real operating system like linux and we will get more interesting things from him. This is what you can... Continue Reading →
Serverless Computing and Security what to think about. From @mwVme and @gilad_maayan #infosec #serverless #cloudsecurity #security
Really nice article about serverless computing and security problems that needs to get addressed NOW. Found the article at mwhite page but this article was written by Gilad David Maayan, guest writer for the site. But do not forget to look at other posts from Michael White, good stuff! Link to the article from Notes... Continue Reading →
Configure Office365 as a Service Provider in a federation and use Fortinet as Identity Provider. @Fortinet #fortinet #SAML @Office365 #federation @AzureSupport #cloud #cloudsecurity # #fortinet
Hi, a hole different topic today. On the table is federation. In this case we want a third party solution to handle authenticate to Office365. Then we can control all the login function in our own product. Federation talks a specific language that is called SAML ( Security Assertion Markup Language ).More information regarding SAML... Continue Reading →
Install PowerShell on Ubuntu 20.04 and add support for AzureAD. #powershell @ubuntu #linux @Microsoft @Azure #linux-guy-try-windows
Hi I want t run PowerShell on my Ubuntu machine and also add support for Azure. Because soon I will try to set up some federation in Azure. Below is from Microsofthttps://docs.microsoft.com/en-us/microsoft-365/enterprise/connect-to-microsoft-365-powershell?view=o365-worldwideIt is in Swedish but It says that Ubuntu 20.04 is not supported. I will be supported in the 7.1 release. The screenshot is... Continue Reading →
Installing Crowdsec on my hacking rig. How to block unwanted connections. Like bruteforce attacks on ssh. @Crowd_Security @DanielMiessler #hacker #bruteforce #ssh #cybersecurity #Security
I was reading on Daniel Miessler website and got really excited about his article about replacement to fail2ban. https://danielmiessler.com/study/crowdsec/?mc_cid=970356fcef&mc_eid=fa6207cba8 ). Please subscribe to his newsletter, really nice reading. Daniel explains this application in detail and I want to show how I did the installation on my machines. Some difference are there. I wont say it... Continue Reading →
How to install and run Salt from @SaltStack in my hacking rig. @VMware @thehackscast @thatch45 #saltconf @DjJimmyChunga #hacker #automation
Hi again! Today we are gonna take a look at Salt from Saltstack. On Sunday I was walking the dog and was listening to the podcast thehacks. I got very inspired by the podcast and wanted to really try this. I have never seen this product before. I have done some other tests in my... Continue Reading →
Installing Microsoft Edge dev version on ubuntu 20.04. @MicrosoftEdge @EdgeDevTools @ubuntu #linux #ubuntu
Finally (can I say that?) it is edge time on Linux. Really straight forward to get Edge on you Ubuntu 20.04. But I will put this out anyway! This is a dev version so there will be functions that will not work yet. Download package from Microsoft: https://packages.microsoft.com/repos/edge/pool/main/m/microsoft-edge-dev/ Install from cli sudo apt-get install ./microsoft-edge-dev_88.0.673.0-1_amd64.deb... Continue Reading →
Install LogonTracer in my hacking rig. #blueteam @jpcert_en #LogonTracer #ubuntu #linux #infosec #logging #hacking @Docker #logontracer @neo4j
It is time to test LogonTracer from @jpcert_en you can get your copy from https://github.com/JPCERTCC/LogonTracer From the website:LogonTracer is a tool to investigate malicious logon by visualizing and analyzing Windows active directory event logs. We start with a new installation of ubuntu. The servername for this is Logon. The installation is not in this post.... Continue Reading →
Add linux and windows machines to SecurityOnion Kolide Fleet @securityonion #opensource #qsquery #fleet @Kolide #linux @BHinfoSecurity
We have now come so far that we want to add things in my installation of SecurityOnion. And we will start with how to add Linux and Windows boxes to Kolide Fleet. I do not know if this is the right way but after a couple of hours I was able to see the vm:s... Continue Reading →
Installing Security Onion 2.3 in my hacking rig. @securityonion #opensource @Elasticsearch #zeek #grafana #qsquery #wazuh #thehive #playbook #kibana #squert #snort #cortex #fleet #suricata #logstash @BHinfoSecurity @elastic @TheHive_Project @grafana
I must thank @BHinfoSecurity to get my interest in this. There webinars is great, especially 30 minutes before the real webinar begins.Now lets get started. As you have seen I did installation of 16.04 version before. My mistake, to tired! No I have to do this again with the new version. Like 16.04 version this... Continue Reading →
Installing Security Onion 16.04 in my hacking rig. @securityonion #opensource @Elasticsearch #zeek #kibana #squert #snort @BHinfoSecurity @debthedeb
Hi, now after some other installations in my "lab" it is time to look at logging. I got really inspired by webinars from BlackHills, so a big shout out to them. They are doing great work to spread there knowledge to others!And soon I WILL get my backdoor and breaches card game! I do not... Continue Reading →
How to update my hacking rig (Linux and Windows) using ansible. #ansible #ubuntu #linux #infosec #windowsupdate #hacker #automation
I have my vm:s up and running now, but I like my rig to be patched and updated, even if I only have 7 machines I want to centralize update procedure. I have chosen to do this with Ansible. As this is a demo site that I am setting up. Security of some configuration is... Continue Reading →
Hachcat benchmark numbers with a VM with Tesla M60 card PCI passthru. #ubuntu #linux4hackers #hashcat #linux #infosec #hacking #pentest #pentesting #redteam #invida #teslam60
I am running hashcat in a VM (ubuntu 20.04) with a PCI passthru NVIDIA TeslaM60 card. This is my first rig with a graphics card so I have no referense to the numbers below. But here is my benchmark test so you can compare. Running Cuda so I can access all memory on the card.... Continue Reading →
How to access internal machines with ssh tunneling. Tunnel rdp thru a jumpstation with ssh. #infosec #hacking #pentest #pentesting #redteam #linux4hackers #kali #parrotos #linux #linux4hackers #ssh
This is follow up of the previous post regarding my rig. How do I access this where ever I am? I use SSH tunneling for that. If I loose connection for some reason I always use tmux on the target so I can reconnect to the same session as before. We start with a picture,... Continue Reading →
How did I create hacking rig for ethical hacking. Based on VMware with Tesla M60. #infosec #hacking #pentest #pentesting #redteam #hackthebox #tryhackme #linux4hackers #ctf #kali #parrotos #linux #godaddy #linux4hackers
My goal with this project was to create a hacking rig that I can use when doing hackthebox, tryhackme and other ctf:s. I was lucky to get my hands on a server with Tesla M60 card. My other goal was also to have a server that I can use in phishing tests, and show others... Continue Reading →
ESXi 6.7 with ixbgen driver gets admin down on the vmnic when reconnect occurse. #VMware #esxi #ixben #ixbe #vExpert
We had a failure on a core switch and following we got strange issue with our ESXi host that were running HP / Intel nic cards with driver ixgben. The state of the nic was Admin Down on ESXi side. On the switch it was up. FYI we were running IP Hash on the vswitch.... Continue Reading →
Knowledge Update 2020-08-20
Hi!Welcome to the first of many (I hope) knowledge updates from me. My goal is so gather information in one post instead of many posts.Most of this information are from third party and I do not have the time to source review everything. But still I like of sharing my thoughts to you.This first knowledge... Continue Reading →
How to get IPv6 and IPv4 support with proxychain4 running kali. #hack #kali #linux #infosec #hacking #pentest #pentesting #redteam #proxychain4
I wanted to use proxychain with IPv6, ended up with this configuration. If you have not install proxychain4 do that now! Tor configuration file add below /etc/tor/torrc SocksPort [::1]:9050 SocksPort 127.0.0.1:9050 ClientUseIPv6 1 ClientPreferIPv6ORPort 1 ClientPreferIPv6DirPort 1 Proxychain4 configuration file. Add the information below in the file under [ProxyList] /etc/proxychain.conf socks5 :: 9050 socks4 127.0.0.1... Continue Reading →
If you are attending “Getting Started in Security with BHIS and MITRE ATT&CK with @strandjs” next week and running Linux and VirtualBox. How to import the machine? @BHinfoSecurity @WWHackinFest @debthedeb #cybertraining #hackers #CyberSecurity #infosec
I am running Kali and VirtualBox. When running Virtualbox there are some issues. If the machine that you are running AMD this perhaps works. I am running INTEL so that sucks. INTEL + VirtualBox + Wsl v2 = Do Not Work For Me. There is a problem running wsl v2 in VirtualBox with Windows 10.Not... Continue Reading →
How to disable systemd-resolved. Problem to get resolve.conf updated with NetworkManger #ubuntu #networkmanager #linux #INVIDGruppen
When you running systemd-resolved you have entry in /etc/resolv.conf that points to nameserver 127.0.0.53. When you troubleshoot sometimes you do not want this. This is how I did it: Disable systemd-resolved sudo systemctl disable systemd-resolved.service sudo systemctl stop systemd-resolved 2. Edit network-manager settings files /etc/NetworkManager/NetworkManager.conf and dns=default roger@xps13:~$ cat /etc/NetworkManager/NetworkManager.conf [main] plugins=ifupdown,keyfile dns=default [ifupdown] managed=false... Continue Reading →
Powershell and Vmware PowerCLI, get-vm exception has been thrown by the target of an invocation. How to fix and add proxy in powershell. Add PSGallery as a repo.#vExpert #VMware #powershell #vmwarepowercli
Uninstall PowerCLI from VMware (we add it later from PSGallery) Start Powershell Set tls security to 1.2 [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 Set http proxy [Environment]::SetEnvironmentVariable("HTTP_PROXY", "proxy.invid.se:3128", [EnvironmentVariableTarget]::Machine) Set https proxy [Environment]::SetEnvironmentVariable("HTTPS_PROXY", "proxy.invid.se:3128", [EnvironmentVariableTarget]::Machine) Now that we have internet connection you can try in powershell, just for confirmation. wget https://invid.se Now it is time to register PSgallery... Continue Reading →
Spam-test. Test if your email adress / domain are on any blacklist or if anything is wrongly configured. Check for spf,dkim and other stuff. #pentesting #blueteam #cybersecurity #spam #tester
This is a simple way to test if your email security is ok. Open a web browser and access https://mail-tester.com and copy the destination email on the page. Then send a email to that address that you got from the page Then go back to the web page and press Then check your score. (wait... Continue Reading →
Buffer Overflow, how do I prepare for Penetration Testing Professional V5 buffer overflow part. @eLearnSecurity #bufferoverflow #infosec #hacking #pentest #pentesting #redteam #hackthebox #INVIDGruppen #INVID
I am not a programmer from the beginning so I struggle a lot with buffer overflow part of the PTP course. I can not turn back time 25 years and start study programming so how do a old dog learn buffer overflow? This is what I do. Watch Videos, I learn faster if someone tells... Continue Reading →
How to set up juice-shop @ heroku for free. Then begin hacking your own web application. @heroku @owasp #infosec #hacking #pentest #cybersecurity #webhacking
Update 2022-08-25 Seems that this is not gonna be free anymore 🙂 https://blog.heroku.com/next-chapter I was watching a YouTube video from https://twitter.com/thecybermentor and wanted to spread the word to my 2 followers. This is a great way to get started with web application hacking. You will set up your own environment in seconds. After the deployment... Continue Reading →
How to get Bluetooth headset working both as headset and high fidelity playback A2DP Sink with nice sound. @system76 #Pop!_OS #linux #pop_os #ubuntu #Linux #gnome
I was unable to switch my bluetooth headset between different audio profiles. Did read alot of blogs and edit blutooth and pulsaudio files to get this to work. Did not get sound in the headset when I went into settings and test my sound. It says that I test my headphone but the sound went... Continue Reading →
How to get systray icons for programs. @system76 #Pop!_OS #linux #pop_os #ubuntu #Linux
I installed Pop!_OS, clean install. After that I installed some application that uses system tray. But some icons do not show up. I am running latest version and DELL XPS 13 9370. I does not matter what extension I enable. Fix that works Install gnome-tweaks sudo apt-get install gnome.tweaks 2. Now install system tray extension... Continue Reading →
Create file with hostnames from website with cewl, then scan the webserver for vhosts with Metasploit vhost_scanner to find hidden virtual hosts on webserver. #infosec #hacking #pentest #pentesting #redteam #hackthebox #ctf #linux4hackers
We start to collect possible hostnames from websites with Cewl cewl http://10.10.10.1 -w cewl.txt You can also use some other switches like -d = deph to look on the website for words -m = minimum wordlengh -w = outputfiel So that the final command can look like this: cewl http://10.10.10.1 -d 5 -w cewl.txt When... Continue Reading →
Copy vswitch vlan from one host to another with powershell. @VMware #vExpert #esxi #VMware
This simple powershell scripts copy vlans from one server to another. With this script I needed to manually create the vmotion network after. But all other vlans was ccreated. Start Powershell In this case I was running linux. pwsh Set-PowerCLIConfiguration -InvalidCertificateAction Ignore -Confirm:$false Connect-VIServer cmdlet Connect-VIServer at command pipeline position 1 Supply values for the... Continue Reading →
Terminator + tmux = perfect match? Starting and attaching tmux sessions from terminator automatic with bash. @kalilinux #kali #kalilinux #linux#linux4hackers #linux #tmux #terminator #infosec #hacking #pentest #pentesting #redteam
My goal was to start Terminator, that's the terminal program I use and the reattach to tmux sessions in the three windows that I have. If I close terminator and started it again I wanted the tmux sessions to reattach to the old ones. And I i close tmux I wanted the same tmux windows... Continue Reading →
Upgrading VirtualCenter to 6.7.xx you get: Error in method invocation Timeout happens while sending message to microservice #vsphere #vcenter @vmware
I did get this on 2 different upgrade I did I tried two methods both worked for me. Reboot VirtualCenter server and do the upgrade again Or ssh into the VirtualCenter box and type: rm /var/run/vmware/applmgmt/update_microservice.pid Upgrade again!
Running Linux, is it possible to use OneDrive and Google Drive. Yes and it works. #linux #onedrive #googledrive #insync @insync
I do not say anything about security issue regarding this, but I needed a way to sync my Companies OneDrive and my private stuff to Google Drive. I tried a lot of different cli application, but those did not work for me. I have now found an application that works, and I only need one... Continue Reading →
How to import missing key from all the repository in a one liner. @kalilinux #kali #kalilinux #linux #gpgkey #NO_PUBKEY
You get this error when you apt-get update The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 1A1C1C101311121 How to import missing gpg key from all the repository in a oneliner. Thanx to https://www.linuxuprising.com/2019/06/fix-missing-gpg-key-apt-repository.html sudo apt update 2>&1 1>/dev/null | sed -ne 's/.*NO_PUBKEY //p' | while read key; do if... Continue Reading →
CORE-IT is a FREE virtual conference hosted by Chappell University. The online event begins March 24th at 9 am Pacific Time. #wireshark #nmap #darknet @torproject #kismet #tcp #dns @LauraChappell https://www.engagez.net/coreit1#lct=entrance
I got an email regarding a free Virtual Conference 2020! Could be something real nice! https://www.engagez.net/coreit1#lct=entrance Agenda here: https://coreit.s3.amazonaws.com/CORE-IT_Agenda-v1f.pdf https://coreit.s3.amazonaws.com/CORE-IT_Agenda-v1f.pdf https://coreit.s3.amazonaws.com/CORE-IT_Agenda-v1f.pdf https://coreit.s3.amazonaws.com/CORE-IT_Agenda-v1f.pdf https://coreit.s3.amazonaws.com/CORE-IT_Agenda-v1f.pdf
ESXTOP on esxi server get really screwed up in terminal. Running from Linux. @vExpert #esxtop #linux #VMware #vmug #terminal
I was troubleshooting a ESXi host with esxtop, but the terminal was screwed up. The thing to set is this: TERM=xterm Then run esxtop again and it all locked nice.
Refresh computer group membership without reboot on Windows #windows #gpupdate #kerberos #pentest #hacking #redteam
Remove cached kerberos ticket klist -lh 0 -li 0x3e7 purge Update gpupdate /force Logout / Login
Fishing with Raspberry Pi, Kali, Auto connect to VPN, Auto register domain with GoDaddy, Automatic SSL cert with Letsencrypt, Run Golang, Run Gophish @letsencrypt @golang @kalilinux @GoDaddy #kali #raspberrypie #linux #infosec #hacking #pentest #pentesting #redteam #gophish
This is just for demo, I used root as user, you should perhaps consider other user to do this. Installation of Kali Download Kali Image https://www.offensive-security.com/kali-linux-arm-images/ Flash the SDCARD with etcher on you Kali box or any other burning program. Put the sdcard in the PI and boot OpenVPN Autostart Download opvpn conf file from... Continue Reading →
Virtual Box empty gui when running darkmode in Linux. @kalilinux #kali #kalilinux #linux #VirtualBox
When you start Virtualbox in darkmode theme, you do not see anything in the gui. Start VirtualBox with a style... Available styles: cleanlooks, gtk2, cde, motif, plastique, Windows, Fusion virtualbox -style Windows %U Without Style With Style
How to exploit Active Directory ACL based privilege escalation path with Bloodhound and aclpwn.py. Then collect the hashes, if you are lucky to get that level of access with secretdump.py #kali #kalilinux #hacking #pentest #pentesting #redteam
This was done from Kali box. Of course the Sharphound was ran on a compromised computer. Used application Bloodhound and Sharphound ( https://github.com/BloodHoundAD/SharpHound ) aclpwn ( https://github.com/fox-it/aclpwn.py ) Steps to do it Get output with sharphound and put that on our kali box use -all when run the Sharphound. Start neo4j and bloodhound import the... Continue Reading →
Microsoft change from ldap to ldaps. What will happen to my Vcenter with Integrated Windows Authentication (IWA) customers. #vcenter #vmware #ldap #ActiveDirectory
Integrated Windows Authentication (IWA) has also been tested by VMware Engineering and verified to be compatible with these changes. IWA uses different protocols and mechanisms to interact with Active Directory and is not affected by changes to the Active Directory LDAP servers. Where did I find this information: Microsoft https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV190023 Vmware https://blogs.vmware.com/vsphere/2020/01/microsoft-ldap-vsphere-channel-binding-signing-adv190023.html https://kb.vmware.com/s/article/2149697
Linux Autostart application with delay and also minimize the application after start. #kalilinux #linux
Some application start in full screen and I do not want that. I want them minimized when I login. In this case I am running Kali 2020.1. You need to install a program. sudo apt-get install wmctrl The I did create a app directory in home, In this directory I created app.sh file with the... Continue Reading →
How to turn of power management on the wifi in kali 2010.1 (or any other distro using NetworkManager). @kalilinux #kali #kalilinux #linux #NetworkManager
Sometimes there are issues with speed, performance, lost of connection to access points. This can be helpful in some configurations. Before: iwconfig wlan0 wlan0 IEEE 802.11 ESSID: Mode:Managed Frequency:5.26 GHz Bit Rate=6 Mb/s Tx-Power=20 dBm Retry short limit:7 RTS thr:off Fragment thr:off Power Management:on Link Quality=56/70 Signal level=-54 dBm Rx invalid nwid:0 Rx invalid crypt:0... Continue Reading →
Kali 2020.1 XFCE. Unable to start any program from gui that requires root privilege. Synaptic just do not start. Firewall-applet just say unable to communicate. It starts fine from cli. @kalilinux #kali #kalilinux #linux
I just installed Kali weekly release (2020.1) with KDE and XFCE and all things seems to work very fine. But one thing with XFCE is that when I try to start things fron XFCE that use root permission it wont work. Strange errors or the applications just do nothing. gksu is no longer availble pkexec... Continue Reading →
Compile an exploit on ParrotOS for Windows 32bit. @ParrotSec #infosec #hacking #pentest #pentesting #redteam
I needed to compile an exploit in ParrotOS. Did not have a Windows machine at the moment. In this case it was MS03-26 for 32 bit. Before we begin we need to install some applications in ParrotOS sudo apt install mingw-w64 searchsploit ms03-026 searchsploit -m exploits/windows/remote/100.c x86_64-w64-mingw32-gcc 100.c -o shell.exe -lws2_32
Problem with Nimble plugin in VirtualCenter 6.7U3 or any other plugin. #VMWare #VirtualCenter #nimble #storage
How to completely remove and start from scratch regardning Nimble Plugin in Vcenter. W had the plugin that was in running mode 1 - Unregister the array from VC in Nimble 2- Clean the VC cache SSH to vcenter server shell service-control --stop vsphere-client service-control --stop vsphere-ui cd /etc/vmware/vsphere-client/vc-packages/vsphere-client-serenity rm -rf com.nimblestorage.* cd /etc/vmware/vsphere-ui/vc-packages/vsphere-client-serenity rm... Continue Reading →
Git pull with subdirectories. Instead of every subdirectory one by one.
If you have for example a github directory in our home directory and want to update all the applications at the same time, instead of going in to every subdirectory and git pull from there. You can do every subdirectory at the same time for i in */.git; do ( echo $i; cd $i/..; git... Continue Reading →
How did my journey to Licensed Penetration Tester (Master) Certification begins and ends. My own thoughts. #LPTMaster #penetrationtesting #infosec #eccouncil @ReadynezSocial @ECCOUNCIL
My journey began 2018-07-09 at Readynez ( Örenäs Slott) a rely warm summer week for Sweden anyway, almost 30 degrees Celsius. Here is what I think about about the journey that I choose to take. CEH Course There is a lot talk about this course on social media. But for a beginner like me this... Continue Reading →
How to get VMware Remote Console on Kali 2019.4
Thanx to Dave Parker http://computersalad.blogspot.com/2018/09/using-vmware-remote-console-on-debian.html sudo su cd /usr/lib/vmware/bin mv vmrc vmrc.old Create a new vmrc file in /usr/lib/vmware/bin with this content #!/bin/bash LIBDIR="/usr/lib/vmware/lib" BINDIR="/usr/lib/vmware/bin" LD_LIBRARY_PATH="" for dir in $(find ${LIBDIR} -type d) ; do LD_LIBRARY_PATH="${dir}:${LD_LIBRARY_PATH}" done export LD_LIBRARY_PATH ln -s ${BINDIR}/appLoader /tmp/vmrc /tmp/vmrc $* rm -f /tmp/vmrc exit 0
Autostart links with OneGate, Tunnel, HTML5 and Web resources.
This is how you create autostart links with OneGate. If you are runing the lates version and https only, change http to https. Tunnel http://onegate.invid.se.se/mg-local/autostart?resource=mg-local&uri=/mg-local/jretestifneeded?path=https:/rdp-server01.onegate.invid.se/parameters?resource=rdp-server&port=33891&cpopup=no&client=/mg-local/terminalserver/terminalserver-wrapper.html&p1=TRUE&p2=TRUE&p3=TRUE&p4=FALSE&p5=TRUE&p6=1280&p7=1024&p8=TRUE&p9=TRUE&p10=&description=asdfvbm9taXNlcasdfasdfasdfw=&logintype=webtoken HTML http://onegate.invid.se/mg-local/autostart?resource=rdp-server&uri=/mgdev-gw&logintype=webtoken Webresurs http://onegate.invid.se/mg-local/autostart?resource=www-server&uri=/page&formfill=false&logintype=webtoken
Get VM on what Datastore and what DRS group the VM is member of, export the result and email to you in a oneliner.
Special thanks to my better looking colleague @ http://blogg.schillman.se/ He is a powershell guru! I did this on Linux so I do not have the power to store username and password. But I know that you can do this if you are running Windows! If the vmware modules are not installed: Start powershell Set-PowerCLIConfiguration -InvalidCertificateAction:Ignore... Continue Reading →
How to restart http/https on Brocade sanswitch.
You need to login with root account on the switch. SAN-SWITCH1:root> /fabos/libexec/webdconfigure http attributes (yes, y, no, n): [no] y HTTP Restart (yes, y, no, n): [no] y HTTP enabled (yes, y, no, n): [yes] y ErrorLog Enabled (yes, y, no, n): [no] AccessLog Enabled (yes, y, no, n): [no] SSLLog Enabled (yes, y, no,... Continue Reading →
Cloned vm is pionting to original vm disks, and you get error when powering on cloned vm, File system specific implementation of LookupAndOpen[file] failed.
(We are using old version of VCenter Server 6.5 Update 1e), Yes, we are about to upgrade! When you clone a machine in HTML5 it failes to powered on the cloned machine, this works when you are using Flash client. In HTML5 the cloned machine still points to the original vmdk files. In Flash it... Continue Reading →
Add & Remove VM from DRS Groups based on datastore. Using PowerShell Ubuntu 19.10 Budgie. Add-DrsVMtoDrsVMGroup and Remove-DrsVMFromDrsVMGroup
Thanks to Author: Tim Carman Twitter: @tpcarman Github: tpcarman https://www.timcarman.net/2017/10/27/add-remove-virtual-machines-based-datastore-location-powercli/ Functions: Add-DrsVMtoDrsVMGroup Remove-DrsVMFromDrsVMGroup install Powershell Get PowerShell to work with ubuntu 19.10 Budgie Create Powershell Profile Run it! sudo snap install powershell --classic export DOTNET_SYSTEM_GLOBALIZATION_INVARIANT=1 vi /home/USERNAME/config/powershell/Microsoft.PowerShell_profile.ps1 Paste the following in the file: $Hour = (Get-Date).Hour If ($Hour -lt 12) {"Morning Master"} ElseIf ($Hour -gt... Continue Reading →
Getting Powershell to work with Ubuntu 19.10 (budgie). Couldn’t find a valid ICU package installed on the system
You get error like this: Process terminated. Couldn't find a valid ICU package installed on the system. Set the configuration flag System.Globalization.Invariant to true if you want to run with no globalization support. Did not work with powershell preview sudo snap install powershell --classic export DOTNET_SYSTEM_GLOBALIZATION_INVARIANT=1 pwsh
Ubuntu Budgie 19.10 mousepad right click how to switch from two finger click.
Standard is to use 2 finger and click to get right mouse click. You can switch to "standard" Right click on mouse pad: gsettings set org.gnome.desktop.peripherals.touchpad click-method areas To get back to two fingers click: gsettings set org.gnome.desktop.peripherals.touchpad click-method fingers
Configure snmp for Esxi and Virtual Center Appliance
If you want to monitor your enviroment using snmp you can. I will recommend going to SNMPv3 not v2 like this....but I just wanted to try esxi: esxcli system snmp set --communities secret esxcli system snmp set --port 161 esxcli system snmp set --syslocation SERVERROOM esxcli system snmp set --enable true Virtual appliance: snmp.set --port... Continue Reading →
How to manual replace disk in 3PAR when you get: Proactive Disk Replacement Required: NBD.
We received a new disk from HP because we had proactive failure on disk. If you ssh to 3par, we can not see any alarms,logs or anything that indicates that a disk have proactive failure. In short words: 1.servicemag start 0 1 Failing the drive... Continue Reading →
Ubuntu running Librenms with MariaDB don’t start after 100% disk full.
I am trying out Librenms under Ubuntu 18.04. I did dumb thing and sized the disk to small. So today my disks was used 100%. I expand the disk (lvm) and resize the partitions. But the mariaDB did not start. What I did was, I removed this file /var/lib/mysql/tc.log rm /var/lib/mysql/tc.log systemctl start maridb.services And... Continue Reading →
How to get vDocumentation to work in PowerShell
Start PowerShell as Administrator Install-Module -Name VMware.PowerCLI -Scope CurrentUser Install-Module ImportExcel -scope CurrentUser Install-Module vDocumentation -Scope CurrentUser Set-ExecutionPolicy Unrestricted Set-PowerCLIConfiguration -InvalidCertificateAction Ignore -Confirm:$false Connect-VIServer Then you are up and runnig Great work from Ariel Sanchez Mora https://github.com/arielsanchezmora/vDocumentation Get-Module vDocumentation -ListAvailable | Format-List Get-ESXInventory Document host hardware inventory and host configuration Get-ESXIODevice Document information from HBAs,... Continue Reading →
Get service tag from Linux on Dell machine
sudo dmidecode | grep "Serial Number" You get something like this: Serial Number: 21XHTN1
Edit syslog to save log file on ESXi host you get A general system error
You get an error when editing advanced option on ESXi host (syslog) But when you do this from CLI it work and the option is ok in the GUI also. esxcli system syslog config set --logdir=/vmfs/volumes/DATASTORE01/esx01/
Create a certificate for website in pkc12 format. Combine the intermediate and the certificate and private key.
Create Key file openssl genrsa -des3 -out mg.key 2048 Create CSR with above keyfile openssl req -new -sha256 -key ./cert.key -out ./cert.csr Fill in the questions regarding the csr Send the CSR to the company that issue certificates When you get the certificate back from the cert company you do this Create a all.crt file... Continue Reading →
Upgrade Dell OpenManage Enterpris to 3.2. Console is being updated please wait…
Started the upgrade 08:10 and the upgrade was finished 9:37. I have only about 10 host in OME. I takes long time just wait. Do not forget to delete the snapshot after the upgrade is finnished. The CPU was like this during the time. The screen that was there for a long time was this:... Continue Reading →
VMware Converter 6.2 failed after 3% with error FAILED: An error occurred during the conversion: ‘BlockLevelVolumeCloneMgr::CloneVolume: Detected a write error during the cloning of volume \WindowsBitmapDriverVolumeId=[60-2A-FF-68-00-00-10-00-00-00-00-00]. Error: 37409 (type: 1, code: 2338)’
1 physical server to virtual with VMware Converter 6.2 failed after 3% with error. FAILED: An error occurred during the conversion: 'BlockLevelVolumeCloneMgr::CloneVolume: Detected a write error during the cloning of volume \WindowsBitmapDriverVolumeId=[60-2A-FF-68-00-00-10-00-00-00-00-00]. Error: 37409 (type: 1, code: 2338)' Source machine had Teaming configured and I just pulled out the cabels and put new one in... Continue Reading →